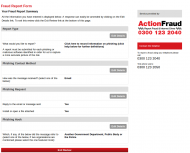
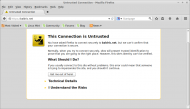
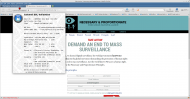
Today’s Register has an article about the UK Internet Service Providers Association written evidence to the Parliamentary Joint Committee on the Draft Investigatory Powers Bill. I don’t wish to comment on that evidence here, Adrian Kennard has already provided much useful comment on the failings of the Draft Bill. My purpose in this post to …
Category: security
Permanent link to this article: https://baldric.net/2016/01/07/idiotic/
Dec 24 2015
merry christmas 2015
It’s trivia’s birthday again (9 years old today!), so I just have to post to wish my readers (both of you, you know who you are….) a Merry Christmas and a happy New Year. Much has happened over the last year or so which has distracted me from blogging (life gets in the way sometimes) …
Permanent link to this article: https://baldric.net/2015/12/24/merry-christmas-2015/
Dec 08 2015
knees and other jerks
On sunday, the motherboard intially reported that, in the wake of the Paris atrocities of November 13th, the French Government was proposing to ban Tor and free WiFi. As it turns out, this is not strictly accurate. The report was later corrected – thus: Correction: The initial headline and copy of this article suggested that …
Permanent link to this article: https://baldric.net/2015/12/08/knees-and-other-jerks/
Nov 23 2015
christmas present
Like most people in the UK at this time of the year I’ve been doing some on-line shopping lately. Consequently I’m waiting for several deliveries. Some delivery companies (DHL are a good example) actually allow you to track your parcels on-line. In order to do this they usually send out text or email messages giving …
Permanent link to this article: https://baldric.net/2015/11/23/christmas-present/
Oct 29 2015
lancashire police fail
This is simply depressing. Today I received a classic phishing attack email – the sort I normally bin without thought. According to virustotal, the attachment, which purported to be an MS Word document called “Invoice 7500005791.doc”, was a copy of W97M/Downloader, a word macro trojan which Symantec says is a downloader for additional malware. So …
Permanent link to this article: https://baldric.net/2015/10/29/lancashire-police-fail/
Jun 02 2015
de-encrypting trivia
Well, that didn’t last long. When I decided to force SSL as the default connection to trivia I had forgotten that it is syndicated via RSS on sites like planet alug. And of course as Brett Parker helpfully pointed out to me, self-signed certificates don’t always go down too well with RSS readers. He also …
Permanent link to this article: https://baldric.net/2015/06/02/de-encrypting-trivia/
Jun 01 2015
encrypting trivia
In my post of 8 May I said it was now time to encrypt much, much more of my everyday activity. One big, and obvious, hole in this policy decision was the fact that the public face of this blog itself has remained unencrypted since I first created it way back in 2006. Back in …
Permanent link to this article: https://baldric.net/2015/06/01/encrypting-trivia/
Nov 27 2014
independent hit
On trying to reach the website of the Independent newspaper today (the Grauniad is trying my patience of late), I received the following response: Closing the popup takes you to this page: I haven’t checked whether this is simply a DNS redirect or an actual compromise of the Indy site, but however the graffiti was …
Permanent link to this article: https://baldric.net/2014/11/27/independent-hit/
Sep 26 2014
CVE-2014-6271 bash vulnerability
Guess what I found in trivia’s logs this morning? 89.207.135.125 – – [25/Sep/2014:10:48:13 +0100] “GET /cgi-sys/defaultwebpage.cgi HTTP/1.0” 404 345 “-” “() { :;}; /bin/ping -c 1 198.101.206.138” I’ll bet a lot of cgi scripts are being poked at the moment. Check your logs guys. A simple grep “:;}” access.log will tell you all you need …
Permanent link to this article: https://baldric.net/2014/09/26/cve-2014-6271-bash-vulnerability/
Jul 23 2014
department of dirty
Like most ‘net users I get my fair share of spam. Most of it gets binned automatically by my email system, but of course some still gets through so I am used to hitting the delete button on random email from .ru domains offering me the opportunity to “impress my girl tonight”. Most such phishing …
Permanent link to this article: https://baldric.net/2014/07/23/department-of-dirty/
Apr 16 2014
nsa operation orchestra
In February of this year, Poul-Henning Kamp (a.k.a “PHK”) gave what now looks to be a peculiarly prescient presentation as the closing keynote to 2014’s FOSDEM. In the presentation (PDF), PHK posits an NSA operation called ORCHESTRA which is designed to undermine internet security through a series of “disinformation” or “misinformation”, or “misdirection” sub operations. …
Permanent link to this article: https://baldric.net/2014/04/16/nsa-operation-orchestra/
Apr 15 2014
boot and nuke no more
I was contacted recently by a guy called Andy Beverley who wrote: Hope you don’t mind me contacting you about one of your old blog posts “what gives with dban”. Thought I’d let you know that I forked DBAN a while ago, and produced a standalone program (called nwipe) that will run on any Linux …
Permanent link to this article: https://baldric.net/2014/04/15/boot-and-nuke-no-more/
Apr 08 2014
heartbleed
This is nasty. There is a remotely exploitable bug in openssl which leads to the leak of memory contents from the server to the client and from the client to the server. In practice this means that an attacker can read 64K chunks of memory on a vulnerable service, thus potentially exposing security critical information. …
Permanent link to this article: https://baldric.net/2014/04/08/heartbleed/
Feb 12 2014
checking client-side ssl/tls
At the tail end of last year I mentioned a couple of tools I had used in my testing of SSL/TLS certificates used for trivia itself and my mail server. However, that post concentrated on the server side certificates and ignored the security, or otherwise, offered by the browser’s configuration. It is important to know …
Permanent link to this article: https://baldric.net/2014/02/12/checking-client-side-ssltls/
Jan 22 2014
dis-unity
The “cloud” is achingly trendy at the moment and new companies offering some-bollocks-as-a-service (SBaaS) keep popping up all over the ‘net. Personally I am extremely unlikely to use any of the services I have seen, I just don’t trust that particular business model. I checked out the website for one of these companies today following …
Permanent link to this article: https://baldric.net/2014/01/22/dis-unity-2/
Jan 20 2014
thrust update
I have just run a search for further evidence of the possible compromise at thrustvps and found threads on webhostingtalk, vpsboard, freevps.us and habboxforum amongst others. All of those comments are from people (many, like me, ex-customers) who have received emails like the one I referred to below. So, I guess thrust /do/ have a …
Permanent link to this article: https://baldric.net/2014/01/20/thrust-update/
Jan 18 2014
thrustvps compromised?
I have not used thrust since my last contract expired. I left them because of their appalling actions at around this time last year. However, today I received the following email from them: From: Admin To: xxx@yyy Subject: Damn::VPS aka Thrust::VPS Date: Sat, 18 Jan 2014 03:28:06 +0000 This is a notification to let you …
Permanent link to this article: https://baldric.net/2014/01/18/thrustvps-compromised/
Dec 10 2013
ssl cipher check
My recent explorations of how to strengthen the ssl/tls certificates I use on both trivia and my mail service have given me cause to look for tools to help me test my configuration. The Calomel firefox plugin and sslabs site are very useful for checking HTTPS configurations, but they are fairly specifically aimed at that …
Permanent link to this article: https://baldric.net/2013/12/10/ssl-cipher-check/
Dec 08 2013
where are you now?
The ongoing revelations from Snowden continued recently with reporting in the Washington Post about the NSA’s program to track mobile ‘phone location data. Reporting here and elsewhere suggests that the NSA is gathering nearly 5 billion records a day on the whereabouts of cellphones around the world. That reporting, and its obvious implications, reminded me …
Permanent link to this article: https://baldric.net/2013/12/08/where-are-you-now/
Dec 07 2013
TLS ciphers in postfix and dovecot
A recent exchange amongst ALUG email list members about list etiquette resulted in a flurry of postings on a variety of related topics. I posted a flippant comment about top posting, but did so (deliberately) from my Galaxy tab using Samsung’s default email client which actually forces top posting. Steve responded suggesting that I look …
Permanent link to this article: https://baldric.net/2013/12/07/tls-ciphers-in-postfix-and-dovecot/
Nov 27 2013
necessary and proportionate
Yesterday I received an email from the Open Rights Group asking me to sign an on-line petition set up in collaboration with nearly 300 other organisations. The email said: In 2013, we learned digital surveillance by governments across the world knows no bounds. Their national intelligence and investigative agencies capture our phone calls, track our …
Permanent link to this article: https://baldric.net/2013/11/27/necessary-and-proportionate/
Nov 26 2013
more ninjastiks
In July I noted that a company calling itself Ninjastik had popped up selling what looked to be essentially the Tor Browser Bundle on an 8 Gig stick for $56.95 or a 16 Gig stick for $69.95. As I expected, we have now seen one or two more companies attempting to sell products which leverage …
Permanent link to this article: https://baldric.net/2013/11/26/more-ninjastiks/
Oct 25 2013
Oliver Stone on PRISM
I am a big fan of Oliver Stone movies. Outside the pages of the Guardian and its sister paper the Observer, the level of comment in the UK on NSA/GCHQ surveillance capability remains bizarrely muted. In the US they are at least having a conversation. Whether that conversation results in any sensible decisions, and then …
Permanent link to this article: https://baldric.net/2013/10/25/oliver-stone-on-prism/
Oct 05 2013
that’s completely ludicrous
Glenn Greenwald on Newsnight. The full episode of Newsnight’s report including Greenwald’s interview and comment from Sir David Omand (ex Director GCHQ) can be seen here on BBC’s iplayer. Gordon Corera, the BBC’s Security respondent reports here on the Newsnight episode. As an aside, I was amused by Ross Anderson’s claim that many academics had …
Permanent link to this article: https://baldric.net/2013/10/05/thats-completely-ludicrous/