God help us all.
Jul 23 2019
fsckd
Permanent link to this article: https://baldric.net/2019/07/23/fsckd/
Jul 15 2019
more password stupidity
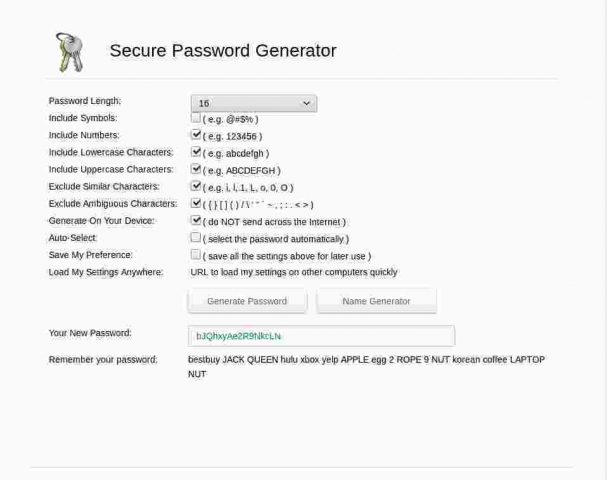
A recent exchange of email with an old friend gave me cause to revisit on-line password/passphrase generators. I cannot for the life of me imagine why anyone would actually use such a thing, but there are a surprisingly large number out there. On the upside, most of these now seem to use TLS encrypted connections so at least the passwords aren’t actually passed back to the requester in clear, but the downside is that most generators are still woefully stupid.
I particularly liked this bonkers example:
Permanent link to this article: https://baldric.net/2019/07/15/more-password-stupidity/
Jul 10 2019
add my name to the list
At the tail end of last year, Crispin Robinson and Ian Levy of GCHQ published a co-authored essay on “suggested” ways around the “going dark problem” that strong encryption in messaging poses Agencies such as GCHQ and its (foreign) National equivalents. In that essay, the authors were at pains to state that they were not in favour of weakening strong encryption, indeed they said:
The U.K. government strongly supports commodity encryption. The Director of GCHQ has publicly stated that we have no intention of undermining the security of the commodity services that billions of people depend upon and, in August, the U.K. signed up to the Five Country statement on access to evidence and encryption, committing us to support strong encryption while seeking access to data. That statement urged signatories to pursue the best implementations within their jurisdictions. This is where details matter, so with colleagues from across government, we have created some core principles that will be used to set expectations of our engagements with industry and constrain any exceptional access solution. We believe these U.K. principles will enable solutions that provide for responsible law enforcement access with service provider assistance without undermining user privacy or security.
Permanent link to this article: https://baldric.net/2019/07/10/add-my-name-to-the-list/
Jul 07 2019
openvpn clients on pfsense
In my 2017 article on using OpenVPN on a SOHO router I said: “In testing, I’ve found that using a standard OpenVPN setup (using UDP as the transport) has only a negligible impact on my network usage – certainly much less than using Tor.”
That was true back then but is unfortunately not so true now.
In 2017 my connection to the outside world was over a standard ADSL line. At its best, I saw around 11 – 12 Mbit/s. Using OpenVPN on my new Asus router I saw this drop to about 10 Mbit/s. I found that acceptable and assumed that it was largely caused by the overhead of encapsulation of TCP within UDP over the tunnel.
Not so.
Permanent link to this article: https://baldric.net/2019/07/07/openvpn-clients-on-pfsense/
Jun 26 2019
one unbound and you are free
I have written about my use of OpenVPN in several posts in the past, most latterly in May 2017 in my note about the Investigatory Powers (IP) Bill. In that post I noted that all the major ISPs would be expected to log all their customers’ internet connectivity and to retain such logs for so long as is deemed necessary under the Act. In order to mitigate this unwarranted (and unwanted) surveillance as much as possible, I wrap my connectivity (and that of my family and any others using my networks) in an OpenVPN tunnel to one of several endpoints I have dotted about the ‘net. This tunnel shields my network activity from prying eyes at my ISP, but of course does not stop further prying eyes at the network end point(s). Here I am relying on the fact that my use of VMs in various European datacentres, and thus outside the scope of the IP Act, will give me some protection. But of course I could be wrong – and as I pointed out in my comparison of paid for versus roll your own VPNs, “there is no point in having a “secure” tunnel if the end server leaks like a sieve or is subject to surveillance by the server provider – you have just shifted surveillance from the UK ISP to someone else.”
Permanent link to this article: https://baldric.net/2019/06/26/one-unbound-and-you-are-free/
Jun 11 2019
back to the gym
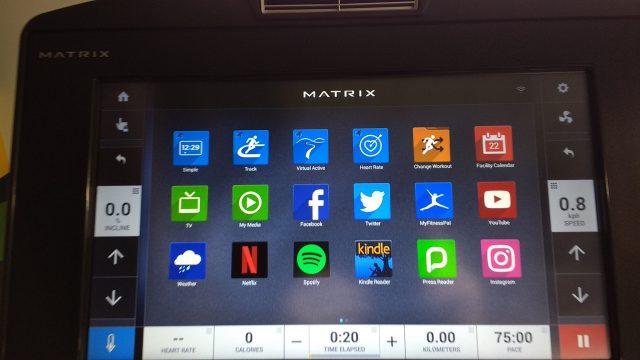
Having just returned from a family holiday which included too much food and drink and nowhere near enough exercise (well, that’s what holidays are for) I needed to get back to the gym in order to work off some of the excess. My local gym has recently undergone a major refurbishment and equipment upgrade and some of the workstations (notably the treadmills) now have integrated touch screens providing access to a variety of services. As you can see from the picture below, these services range from the obviously relevant such as details of your workout, your heartrate or linkages to fitness trackers, through TV, Youtube or Netflix access, to the less obviously necessary social media services such as Facebook, Instagram and Twitter. God knows how you can tweet and run at the same time and it is beyond me why anyone would even consider giving their social media account details to a gym company. But hey, the technology is there and people do use it.
Permanent link to this article: https://baldric.net/2019/06/11/back-to-the-gym/
Mar 21 2019
more in the “you couldn’t make it up” dept
The UK Parliamentary petitions site is currently hosting what appears to be one of the most popular it has ever listed. The petition seeks to gain support for revocation of article 50 so that the UK can remain in the EU. Personal politics aside (though in the interests of transparency I should say that I am a passionate supporter of remain) I believe that this petition, or one very like it, was inevitable given our dear PM’s completely shambolic handling of the whole brexit fiasco. Her latest “appeal” to the “tired” public to get behind her version of brexit in which she lays the blame for the delay to getting her deal over the line in the lap of MPs was probably the last straw for many. It is certainly a risky strategy because she needs the support of those very MPs to get the agreement she wants.
Permanent link to this article: https://baldric.net/2019/03/21/more-in-the-you-couldnt-make-it-up-dept/
Feb 16 2019
postfix sender restrictions – job NOT done
OK, I admit to being dumb. I got another scam email yesterday of the same formulation as the earlier ones (mail From: me@mydomain, To: me@mydomain) attempting to extort bitcoin from me.
How? What had I missed this time?
Well, this was slightly different. Checking the mail headers (and my logs) showed that the email had a valid “Sender” address (some bozo calling themselves “susanne@mangomango.de”) so my earlier “check_sender_access” test would obviously have allowed the email to pass. But what I hadn’t considered was that the sender might then spoof the From: address in the data portion of the email (which is trivially easy to do).
Dumb, so dumb. So what to do to stop this?
Permanent link to this article: https://baldric.net/2019/02/16/postfix-sender-restrictions-job-not-done/
Jan 24 2019
postfix sender restrictions
I mentioned in my previous post that I had recently received one of those scam emails designed to make the recipient think that their account has been compromised in some way and that, furthermore, that compromise has led to malware being installed which has spied on the user’s supposed porn habits. The email then attempts a classic extortion along the lines, “send us money or we let all your friends and contacts see what you have been up to.”
Permanent link to this article: https://baldric.net/2019/01/24/postfix-sender-restrictions/
Jan 23 2019
congratulations to BT
I have been running my own mail server now for well over a decade. Whilst the actual physical hardware (or actually VPS system) may have changed once or twice during that time, the underlying software (postfix and dovecot on debian) has not really changed all that much. However, what has changed over the last decade or so, is the expectation that mail systems will be much more robust, better managed, less insecure (no more “open relays”) and harder on spam than had been the case in the early days of wide takeup of email by the public. Ignoring the “free” offerings from the likes of google, microsoft and others, it would arguably be cheaper, and certainly easier, for me to simply pay for an external mail service by one of the many providers out there. It is pretty easy to find companies offering to host personal email for about a tenner or at most twenty pounds a year. Those “solutions” (as providers seem to love to call their products) usually give you decent anti-spam, A/V scanning, POP3S/IMAPS connectivity (or if you really must, a webmail interface) and can usually alias mail to your preferred domain – particularly if you buy a domain name with your email service. But they always have limitations that I don’t like. The most obvious ones are: restrictions on the number of actual email addresses (as opposed to aliases), limited storage (though that is becoming less of a problem these days), and artificial restrictions on attachment sizes. And I’m bloody minded. I like to control my own email. I run my own email service for the same reason I manage my own DNS, run my own webservers, manage my own wordpress installation, run my own XMPP server and VPNs and manage my own domestic local network with assorted servers hanging off it. I like control and I dislike the opportunity outsourced services have for providing third parties access to my data. My personal data.
Besides, a boy needs a hobby.
Permanent link to this article: https://baldric.net/2019/01/23/congratulations-to-bt/
Dec 24 2018
always keep the address
I normally post a “happy birthday trivia” message at this time of year. Indeed I have been doing this for 12 years now. Of late my posting has become less frequent which is somewhat odd since I now have much more free time than I had back when I started trivia. But no matter – some things are much more important than blogging.
This year I was struck by a BBC article by the poet Ian McMillan which I read yesterday. The article recalls how McMillan briefly met a chap called “Brian” at Jersey airport on a breezy night in autumn many years ago. McMillan was apparently very worried about the impending flight but was reassured by Brian that all would be well. After chatting for a short while and just before boarding the flight, Brian and McMillan swapped addresses and said that they would stay in touch. Unfortunately McMillan then lost Brian’s address. But Brian obviously did not lose McMillan’s address because each Christmas thereafter he sent a card, despite receiving nothing back.
The article ends with McMillan saying:
“Always keep the address. Always remember where people are, and then you can translate those moments of the kindness of strangers into a winter scene and a first class stamp. “
I’d say that was good advice.
Merry Christmas all.
Permanent link to this article: https://baldric.net/2018/12/24/always-keep-the-address/
Dec 12 2018
wordpress 5.0 editor error
When I posted yesterday I noticed that there was a new version (5.0) of wordpress available for installation. So I decided to spend a short while today upgrading as I always do when a new software version is released. But I hit a snag – a big one.
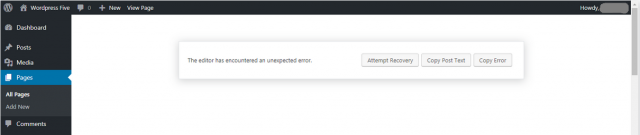
The new version of wordpress includes a completely re-written editor called “gutenberg”. That editor fails quite spectacularly for many users. In my case I could not edit any existing posts or pages and wordpress threw up the error message shown below:
No “attempts at recovery” were successful. So I was left with a broken upgrade and no way to edit any of my existing posts. Not good.
Permanent link to this article: https://baldric.net/2018/12/12/wordpress-5-0-editor-error/
Dec 11 2018
well I never
It’s not often that I find myself agreeing with GCHQ, but ex GCHQ Director Robert Hannigan’s recent comments in an interview with the BBC Today programme struck a chord.
Hannigan headed GCHQ from April 2014 until his resignation for family reasons last year. Whilst in post he pushed for greater transparency at the SIGINT agency. He was responsible for setting up the National Cyber Security Centre in 2017. And in 2016 he argued publicly in favour of strong encryption and against the idea of “back doors” in crypto software. So, arguably, Hannigan is more liberal and open than is common in GCHQ. Certainly his approach was very different to that of his predecessors Iain Lobban or David Pepper.
Permanent link to this article: https://baldric.net/2018/12/11/well-i-never/
Jul 07 2018
re-encrypting trivia
Back in June 2015 I decided to force all connections to trivia over TLS rather than allow plain unencrypted connections. I decided to do this for the obvious reason that it was (and still is) a “good thing” (TM). In my view, all transactions over the ‘net should be encrypted, preferably using strong cyphers offering perfect forward secrecy – just to stop all forms of “bad guys” snooping on what you are doing. Of course, even in such cases there are still myriad ways said “bad guys” can get some idea what you are doing (unencrypted DNS tells them where you are going for example) but hey, at least we can make the buggers work a bit harder.
Permanent link to this article: https://baldric.net/2018/07/07/re-encrypting-trivia/
Feb 18 2018
database failure
In 1909, Franz Kafka wrote the “Inclusion of Private Automobile Firms in the Compulsory Insurance Program” as part of “The Office Writings”. His experience of tortuous bureaucracy in Insurance and elsewhere was later reflected in one of his most famous novels “Der Process” (known in English translation as “The Trial”).
Back in October last year I bought another motorcycle to go with my GSX 1250. I’d just sold three other older bikes and felt the need to fill up the resultant hole in my garage. Besides, a man can never have too many motorcycles. At the time I bought the new Yamaha I spoke to my insurers about getting it added to my existing policy. Unfortunately they had recently changed their systems and I could no longer have one policy covering both bikes. So I took out a new separate policy. Oddly enough, that policy cost me twice as much as I paid for cover on the GSX, a bike with over twice the power and a lot more grunt than my new Yamaha. I was told that whilst /I/ was still the same risk, the underwriters assumed that my Yamaha was a riskier vehicle to insure. The ways of insurers are odd indeed and beyond the ken of mortal man.
Permanent link to this article: https://baldric.net/2018/02/18/database-failure/
Dec 26 2017
Merry Christmas 2017
I’m a couple of days late this year. I normally post on Christmas Eve, trivia’s birthday, but hey, I’ve been busy (it goes with the territory at this time of year if you are a grandparent). This year I thought I would depart from my usual topic(s) and post a couple of pictures marking the occasion. So here you go.
Last year my lady gave me a rather interesting christmas present – a Mr Potato Head, but home made.
Not content to leave the joke alone, this year she went slightly upmarket and gave me a Mr Pineapple Head.
I’m sure she loves me really. In fact I know that she does. She made the toadstool cake below for our daughter’s boys, and hey, she really does love those boys.
Merry Christmas to all my readers, wherever you are (and oddly enough, a lot of you appear to be in China).
Permanent link to this article: https://baldric.net/2017/12/26/merry-christmas-2017/
Oct 14 2017
multilingual chat
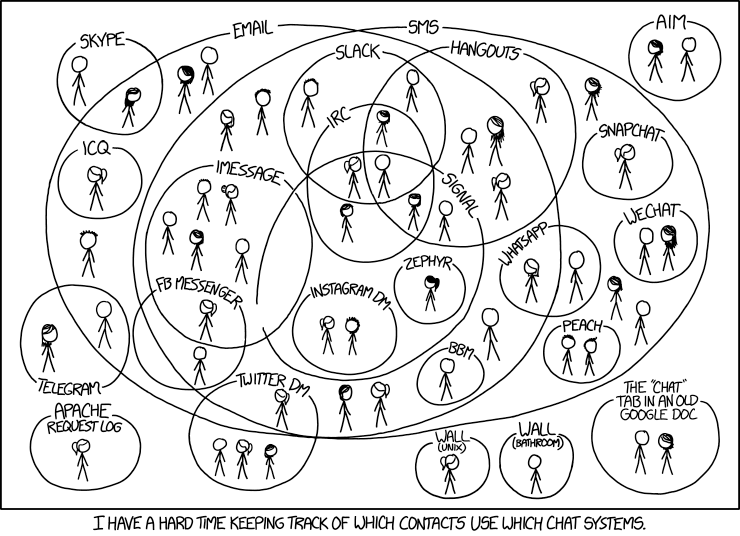
I use email fairly extensively for my public communication but I use XMPP (with suitable end-to-end encryption) for my private, personal communication. And I use my own XMPP server to facilitate this. But as I have mentioned in previous posts my family and many of my friends insist on using proprietary variants of this open standard (facebook, whatsapp etc. ad nauseam). I was thus amused to note that I am not alone in having difficulty in keeping track of “which of my contacts use which chat systems“.
(My thanks, as ever, to Randall Munroe over at XKCD.)
I must find a client which can handle all of my messaging systems. Better yet, I’d like one which worked, and seamlessly synchronised, across my mobile devices and my linux desktop. Even better again, such a client should offer simple (i.e. easy to use) e-to-e crypto and use an open server platform which I can manage myself.
Proprietary systems suck.
Permanent link to this article: https://baldric.net/2017/10/14/multilingual-chat/
Sep 30 2017
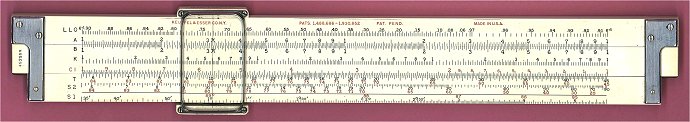
geeks rule
Well, sliderule, actually.
The ‘net is a truly wondrous space. I can’t recall exactly how I stumbled across the “International Sliderule Museum” but it is such a wonderful resource devoted to a tool which most people under the age of 40 will never have used that I just had to post a link to it.
Enjoy.
Permanent link to this article: https://baldric.net/2017/09/30/geeks-rule/
Aug 02 2017
a letter to our dear home secretary
Dear Amber
So,”real people” don’t care about privacy? All they really want is ease of use and a pretty GUI so that they can chat to all their friends on-line? Only “the enemy” (who is that exactly anyway?) needs encryption? Excuse me for asking, but what have you been smoking? Does the Home Office know about that?
I’m a real person. And I care deeply about privacy. I care enough to fund both my own Tor node and various openVPN servers dotted around the world just to get past your ludicrous attempts at gratuitous surveillance of my (and my family’s) routine use of the ‘net. I care about the security and privacy of my transactions with various commercial enterprises, including my bank (which is why I expect them to use TLS on their website). I care about privacy when I correspond with my Doctor and other professionals. I care about privacy when I use an on-line search engine (which, incidentally, is not Google). I care about privacy because privacy matters. I have the right to freedom of thought and expression. I have the right to discuss those thoughts with others of my choice – when I choose and how I choose. You may not like that, but it’s a fact of life. That doesn’t make me “the enemy”. Get over it.
Love and Kisses
Mick
(Note to readers: Aral Balkan has deconstructed Rudd’s ramblings. I commend the article to you.)
Permanent link to this article: https://baldric.net/2017/08/02/a-letter-to-our-dear-home-secretary/
Jun 06 2017
it is now
Back in January 2011, I posted a brief note about a site hosted at the domain “ismycomputeroff.com“. I have just had occasion to look again at that site and found that the domain is now definitely off. It is parked at sedo and is up for sale at the ludicrous price of 599 euros.
Tell you what, you can have my “theinternetisoff.net” domain for the bargain price of half that – after all, it only cost me about a tenner.
[Postscript added February 2020. Since I no longer have this domain, and I chose not to sell it for silly money, you may be able register it yourself if you wish.]
Permanent link to this article: https://baldric.net/2017/06/06/it-is-now/
May 25 2017
monday in manchester
At around 22.30 last Monday, Manchester was subjected to an horrific attack at a pop concert. As the world now knows, a suicide bomber deliberately targeted young people and their friends and families as they were leaving a concert by the young pop singer Ariana Grande. In that attack, 22 people, including children as young as 8 years old lost their lives. Many, many more received life changing injuries.
This is the first confirmed suicide bombing attack in the UK since 7 July 2005. On that day, 12 years ago, I was working in London. I can vividly recall the aftermath of that attack. Shock, horror, disbelief, later turning to anger. But I also vividly recall the reactions of Londoners and visitors to London I met, talked to or simply listened to over the days that followed. Only a few days after the 7th I was travelling by bus to a meeting when quite unbidden a middle aged American couple, obviously tourists, told me and everyone else on the bus that they shared our pain and that they were praying for us. I am not a religious man, indeed, I have no faith whatsoever, but I was deeply moved by that couple’s sincerity. Later, towards the end of July, my wife and I were travelling by Tube towards St Pancras on our way to Paris for our wedding anniversary. The driver of that Tube welcomed us (and everyone else) aboard the “up yours al-Qaeda express”. This show of defiance in the face of horror actually raised a number of smiles from those around us. London survived, Londoners endured.
The citizens of Manchester are now all facing profound shock and grief. That shock and grief will also be felt by anyone who has any shred of humanity within them. London was bad – 52 people lost their lives in that series of co-ordinated attacks. But somehow, Manchester feels worse, much worse. The London bombers targeted morning Tube and bus travellers – mainly commuters, some of whom were late for work because of earlier rail disruption that day. They were a soft target. But the Manchester bombing was callously and deliberately aimed at the ultimate soft target – kids; youngsters and their families emerging from what should have been a wonderful night out. Kids simply enjoying themselves at a concert many would have been planning for and looking forward to for months. Ariane Grande’s fanbase is primarily young women and girls. The attacker would have known that and yet he deliberately chose to detonate his bomb at that time and that place. He, and any accomplices he may have had, deserve nothing but our contempt. Manchester will survive, and Mancunians will endure. They have faced this before in the IRA truck bombing in June 1996. That attack didn’t break them. This one won’t either.
Meanwhile, everyone must grieve for the loss of so many young lives in such a pointless, pitiless attack. My thoughts, and those of my family, are with Manchester.
Permanent link to this article: https://baldric.net/2017/05/25/monday-in-manchester/
May 12 2017
using a VPN to take back your privacy
With the passage into law of the iniquitous Investigatory Powers (IP) Bill in the UK at the end of November last year, it is way past time for all those who care about civil liberties in this country to exercise their right to privacy.
The new IP Act permits HMG and its various agencies to surveil the entire online population. The Act actually formalises (or in reality, legalises) activity which has long gone on in this country (as in others) in that it gives LEAs and others a blanket right of surveillance.
The Act (PDF) itself states that it is:
“An Act to make provision about the interception of communications, equipment interference and the acquisition and retention of communications data, bulk personal datasets and other information; to make provision about the treatment of material held as a result of such interception, equipment interference or acquisition or retention; to establish the Investigatory Powers Commissioner and other Judicial Commissioners and make provision about them and other oversight arrangements; to make further provision about investigatory powers and national security; to amend sections 3 and 5 of the Intelligence Services Act 1994; and for connected purposes.”
(Don’t you just love the “connected purposes” bit?)
Permanent link to this article: https://baldric.net/2017/05/12/using-a-vpn-to-take-back-your-privacy/
Apr 27 2017
free Dmitry Bogatov
Dmitry Bogatov, aka KAction, is a Russian free software activist and mathematics teacher at Moscow’s Finance and Law University. He was arrested in Russia on 6 April of this year and charged with extremism. He is currently held in a pre-trial detention centre, and is apparently likely to remain there until early June at least, while investigations continue. The Russian authorities claim that Bogatov published messages on a Russian website, “sysadmin.ru”, inciting violent action at the opposition protest demonstration held in Moscow on 2 April.
Bogatov is well known in the free software community as a contributor to debian. As a privacy activist he runs a Tor exit node in Russia and it is this latter point which would appear to have caused his difficulty. Apparently, Bogatov’s Tor exit node was logged as the source address for the inflammatory posts in question. The debian project have taken the precaution of revoking Bogatov’s keys which allow him to post material to the project. They see those keys as compromised following his arrest and the seizure of his computing equipment.
Bogatov claims (with some justification it would appear) that he had nothing to do with the posts of which he is accused. Indeed, at the time of the post from his Tor node he claims that he was at a gym with his wife and visited a supermarket immediately afterwards. CCTV footage from the store supports this claim.
Operating a Tor node is not illegal in Russia, nor is it illegal in many other jurisdictions around the world. However, the act of doing so can draw attention to yourself as a possible “dissident” wherever you may live.
I am a passionate fan of free software, I use debian (and its derivatives) as my preferred operating system. I am an advocate of privacy enhancing tools such as GPG, Tor and OpenVPN, and I run a Tor node.
I hope that Dmitry Bogatov is treated fairly and in due course is proved innocent of the charges he faces. I post this message in support.
Permanent link to this article: https://baldric.net/2017/04/27/free-dmitry-bogatov/
Mar 18 2017
pwned
I recently received a spam email to one of my email addresses. In itself this is annoying, but not particularly interesting or that unusual (despite my efforts to avoid such nuisances). What was unusual was the form of the address because it contained a username I have not used in a long time, and only on one specific site.
The address took the form “username” <realaddress@realdomain> and the email invited me to hook up with a “hot girl” who “was missing me”. The return address was at a Russian domain.
Intrigued as to how this specific UID and address had appeared in my inbox I checked Troy Hunt’s haveibeenpwned database and found that, sure enough, the site I had signed up to with that UID had been compromised. I have since both changed the password on that site (too late of course because it would seem that the password database was stored insecurely) and deleted the account (which I haven’t used in years anyway). I don’t /think/ that I have used that particular UID/password combination anywhere else, but I’m checking nonetheless.
The obvious lesson here is that a) password re-use is a /very/ bad idea and b) even old unused accounts can later cause you difficulty if you don’t manage them actively.
But you knew that anyway. Didn’t you?
Permanent link to this article: https://baldric.net/2017/03/18/pwned/