I run my own mail server for a number of reasons. And I rarely regret that decision. However, there have been occasions in the past when relying on a single mail provider (even when that provider is myself) has proven problematic. The first problem arose several years ago when the ISP which I use for my main VPS (Bytemark) had a few technical problems which took my mail server off-line. Like most ISPs these days, Bytemark do most of their business via email. With my email out, I couldn’t correspond with the provider. My second problem was caused by AOL who cannot run a mail service to save their lives. Oddly many of my old friends use AOL and I correspond with those friends “in bulk” (via a list of sorts – those friends are in my old bike club). For some reason known only to AOL they periodically decide that my email service is hostile (possibly a source of spam). It isn’t and my email server appears on no know RBLs. Only AOL treat it as suspect and bounce my email to multiple friends. Oddly, individual emails addressed to only one or two of those AOL users at a time works fine.
Obviously I needed a backup email system. Gmail? You have to be joking. Outlook? Only if I want to pretend to be Linus. So I needed a backup service which I could trust, which was advert free and which I could use simply as a fallback from my main email on my own domains. Lavabit met that requirement and I have used their service very happily on and off for some time. Yesterday I couldn’t reach their server and a message on their website said that POP3 access was offline. Today I learned that Ladar Levison, the owner/operator has taken the service down completely.
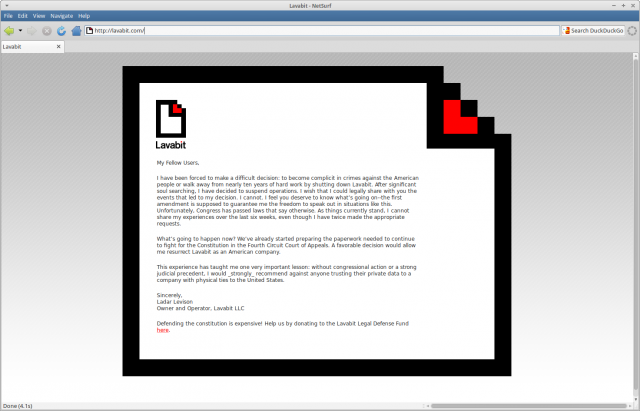
Levison says on the front (and now only) page of the Lavabit site:
This experience has taught me one very important lesson: without congressional action or a strong judicial precedent, I would _strongly_ recommend against anyone trusting their private data to a company with physical ties to the United States.
Silentcircle, another provider of secure communications services has today also decided to shut down its email service. A note on their blog says:
Silent Mail has thus always been something of a quandary for us. Email that uses standard Internet protocols cannot have the same security guarantees that real-time communications has. There are far too many leaks of information and metadata intrinsically in the email protocols themselves. Email as we know it with SMTP, POP3, and IMAP cannot be secure.
And yet, many people wanted it. Silent Mail has similar security guarantees to other secure email systems, and with full disclosure, we thought it would be valuable.
However, we have reconsidered this position. We’ve been thinking about this for some time, whether it was a good idea at all. Today, another secure email provider, Lavabit, shut down their system lest they “be complicit in crimes against the American people.” We see the writing the wall, and we have decided that it is best for us to shut down Silent Mail now. We have not received subpoenas, warrants, security letters, or anything else by any government, and this is why we are acting now.
So, as Neelie Kroes said, bang goes the US cloud service model. Fortunately I do not personally have any data I care about in any US based service. My US VMs are only used as Tor nodes or tails mirrors. Unfortunately I do not know whether any third party which holds data about me I care about does hold that data in the US.
But I’ll bet there are a few.

1 comments
No worries, once we’re online you’ll get a friend-of-the-house account from me.
Actually, I predicted these events for US based companies a couple of years ago. Every single US based company has the same problem: their combination of laws (USA PATRIOT Act, FISA, CALAE and even ECPA) renders any security measure irrelevant, as they still have to comply with the law.
Providers of software and solutions can be legally forced to silently install a backdoor, or face closure or prosecution for non-compliance (Lavabit actually has a problem insofar that it disclosed such a request), and US based companies who use such solutions can simple be told to unlock the required data or have the same problems as the suppliers.
In short, if it is of US origin, there is no longer a way to invest any trust in it. US providers have been enthusiastically giving that problem the ostrich treatment (stuck their heads in the sand and pretended it wasn’t affecting them), with only some paying some marginal attention to the issue by declaring that the US authorities would never get their data because they hosted it elsewhere. Doesn’t work: if your HQ is in the US it means your decision power resides there, rendering that defence meaningless. At slashdot there is at present Yet-Another_NSA_solution being discussed (lock-box.com), well, same problem.
You cannot program around a LEGAL problem…