My previous two posts discussed the need for encrypted DNS and then how to do it on a linux desktop. I do not have any Microsoft systems so I have no idea how to approach the problem if you use any form of Windows OS, nor do I have any Apple devices so I can’t provide advice for iOS either, but I do use Android devices. All my mobile phones for some time have been re-flashed to run a version of Android’s OS software. My current mobile (and two previous ones) run lineageOS, earlier phones used the (now discontinued) cyanogenmod ROM. I dislike google’s cavalier approach to user privacy, but I do like the flexibility and usability provided by modern smartphones. Apple devices strike me as hugely overpriced and I have never been convinced by the “oooh shiny” adoration shown by some of Apple’s hardened admirers. But each to their own.
I tend to buy mid-range smartphones, SIM free and unlocked, costing around the £100-£200 mark or higher specification models second hand. When choosing a new phone I always check whether it will support a current version of lineageos (preferably the latest which is at 17.1, or Android 10). In fact the only reason I have to upgrade my phone is if it becomes unsupported by the OS of my choice. Of course, this happens with mainstream Android on many devices simply because the Telco providing the service stops providing OTA upgrades to the OS (they want you to buy a new “shiny, shiny” and sign a new contract). Fortunately for people like me this often means that we can then get fairly well specced phones second hand and then re-flash them with our preferred OS.
All that aside, prior to Android 9, it was quite difficult to reliably change the DNS settings on such a device. You could, of course have used a VPN app, but several of those actually leak DNS and there was no single central setting which enabled the user to change DNS settings for both WiFi and mobile data. Of course, changing the DNS settings on your home DHCP server (often your WiFi router) would help, but that still left you exposed to the default settings offered by your mobile provider or the WiFi hotspot in your local cafe when out and about. Several apps are (still) available to allow users to change DNS settings but some of those need the phone to be rooted, and this sort of change is often beyond the average normal user. A search for “DNS changer apps for android” will give you several lists of such apps if you are stuck on a device with an android version lower than 9. However, bear in mind that whilst these apps may allow you to change the DNS away from the defaults provided by your ISP or Telco, they will not offer any form of encryption, and many of the apps provide default settings to services which are less than privacy conscious – google on 8.8.8.8 is a common default.
To their credit, in Android 9, Google introduced a “private DNS” option to the central settings. And of course, lineageos 16 and later offers the same functionality. Here’s how:
1. Open “settings”
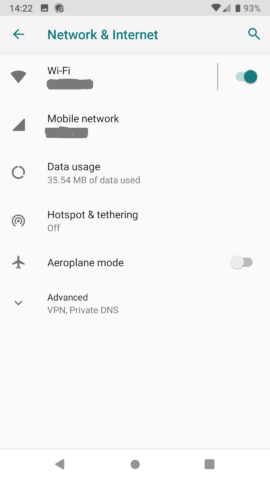
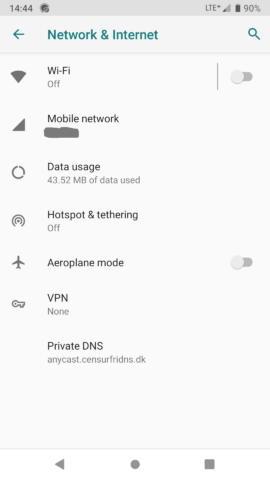
2. Select “Network & Internet”
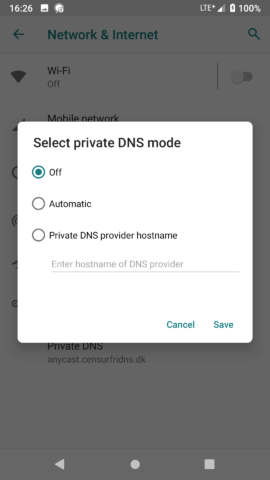
3. Select “Advanced” then “Private DNS”
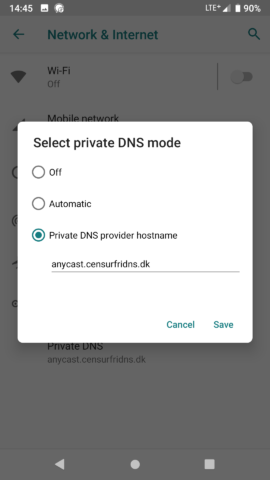
4. On the pop-up screen change “Off” (or “Automatic”) to “Private DNS Provider hostname” and add your preferred provider.
5. Save and exit.
The DNS provider I chose is “anycast.censurfridns.dk” – a service provided by UncensoredDNS. The owner of that system has this to say about his service.
UncensoredDNS was started in November 2009 shortly after I began working at an ISP where one of my responsibilities was to administer the censored DNS servers that all Danish ISPs run for their customers.
I had never been a fan of the Danish DNS censorship system, and working with it first hand didn’t exactly help. At the time OpenDNS was kind of new and Google DNS didn’t exist yet. Friends and family were coming to me asking for a recommendation for an alternative to the censored ISP DNS servers.
Back then OpenDNS did NXDOMAIN redirection, an advertising trick where misspelled nonexistant domains are redirected to a search page with ads instead of returning an NXDOMAIN error. To a DNS purist like myself this made OpenDNS as appealing as a turd on a stick. They also didn’t have ipv6 or DNSSEC, both of which were mandatory on a modern DNS server, even back in 2009.
Even if Google DNS had existed back then I wouldn’t have felt comfortable recommending them either. While they do run a stable, fast and uncensored service, I am not convinced that it is a good idea to hand over all your DNS lookups to Google. They already have all your searches, you might have one of their phones in your pocket, and so on.
All this prompted me to do something about the situation so I started UncensoredDNS with help from friends. After a while I also started giving talks about the service at various conferences, since people naturally have an easier time trusting a service if they know who is behind it. You can see some of my old talks online, for example from RIPE65.
You could of course choose any provider offering DoT services and you can find suggestions on both the dnsprivacy and privacytools sites. Whichever provider you choose, I recommend you stay away from any which log you, or which have less than satisfactory privacy policies (I’m looking at you google).
One final point, for users of Apple’s iphone, the privacytools site recommends an encrypted DNS client for iOS called “DNSCloak”. I have no personal experience of that client, but I am impressed overall by the guys at privacytools.