When I logged on to my new bank site this morning, I tried the “help” offered on the opening screen just to see what they had to say about the range of options available. I was not best pleased to be greeted by the message “Flash is not installed, is not enabled or is not …
Category: security
Permanent link to this article: https://baldric.net/2012/03/06/banking-stupidity/
Mar 04 2012
am I kidding myself
I have recently moved my bank current and short term savings accounts. Partly this is a political statement in support of the move your money campaign, and partly because I feel that my money might actually be a bit safer (if only slightly) in a small UK Mutual than with the UK arm of a …
Permanent link to this article: https://baldric.net/2012/03/04/am-i-kidding-myself/
Jan 12 2012
t-mobile resets its policy?
As I have mentioned in other posts here, I run my own mail server on one of my VMs. I do this for a variety of reasons, but the main one is that I like to control my own network destiny. Back in October last year I noticed an interesting change in my mail experience …
Permanent link to this article: https://baldric.net/2012/01/12/t-mobile-resets-its-policy/
Dec 19 2011
tunnelling X over ssh
OK, yes, I know there are probably already a gazillion web pages on the ‘net explaining exactly how to do this, but I got caught out by a silly gotcha when I tried to do this a couple of days ago, so I thought I’d post a note. Firstly, X is not exactly a secure …
Permanent link to this article: https://baldric.net/2011/12/19/tunnelling-x-over-ssh/
Jan 23 2011
click here
The Cory Doctorow article referenced at the end of the post below mentions URL shorteners as potentially dangerous because they completely obscure the actual URL you will be taken to if you click them. By way of experiment I thought I’d post one here just to see how often it is used.
Permanent link to this article: https://baldric.net/2011/01/23/click-here/
Jan 23 2011
damn, I think I got hit by a 419er
I am normally pretty careful about my on-line security and privacy. I take a lot of care to ensure that my home network is nailed down tightly and all the clients and servers on it are also nailed down as well as I know how. I don’t use software which is susceptible to the majority …
Permanent link to this article: https://baldric.net/2011/01/23/damn-i-think-i-got-hit-by-a-419er/
Jan 04 2011
critical security update to wordpress
This blog comes to you courtesy of those excellent free open source authors who have contributed to wordpress. Unfortunately, in common with all software, wordpress inevitably has some bugs. Worse, some of the those bugs can occasionally be sufficiently bad as to make the software vulnerable to remote exploitation by ne’er do wells and other …
Permanent link to this article: https://baldric.net/2011/01/04/critical-security-update-to-wordpress/
Sep 25 2010
professional ability
I was skimming through a series of security related sites last week when I came across an article referring to someone described as something like “A Person, M.Inst.ISP, CISM, CISSP, MBCS, CITP, BSc, Director of etc…..” and I found myself wondering what that all actually meant. Yes, I know what the letters stand for, hell …
Permanent link to this article: https://baldric.net/2010/09/25/professional-ability/
Aug 27 2010
update to autossh – or how ServerAliveInterval makes this unnecessary
I had a couple of comments on my earlier post about autossh which suggested that I should look at alternative mechanisms for keeping my ssh tunnel up. Rob in particular suggested that setting “ServerAliveInterval” should work. Oddly I had tried this in the past whilst trying out various configuration options and I swear it didn’t …
Permanent link to this article: https://baldric.net/2010/08/27/update-to-autossh-or-how-serveraliveinterval-makes-this-unnecessary/
Aug 01 2010
autossh – or how to use tor through a central ssh proxy
Since I first set up a remote tor node on a VPS about this time last year, I have played about with various configurations (and used different providers) but I have now settled on using two high bandwidth servers on different networks. One (at daily.co.uk) allows 750 Gig of traffic per month, the other (a …
Permanent link to this article: https://baldric.net/2010/08/01/autossh-or-how-to-use-tor-through-a-central-ssh-proxy/
Jul 04 2010
scroogle is having a problem
I posted a note about scroogle back in January. Scroogle offered an SSL interface to the google engine, and, moreover, didn’t lumber its users with google cookies and sundry other irritations. Since then, however, google themselves have started to offer an SSL interface and, coincidentally, scroogle seem to have started to have some problems. If …
Permanent link to this article: https://baldric.net/2010/07/04/scroogle-is-having-a-problem/
Jan 22 2010
tor server compromise
According to this post by Roger Dingledine, two tor directory servers were compromised recently. In that post Dingledine said: In early January we discovered that two of the seven directory authorities were compromised (moria1 and gabelmoo), along with metrics.torproject.org, a new server we’d recently set up to serve metrics data and graphs. The three servers …
Permanent link to this article: https://baldric.net/2010/01/22/tor-server-compromise/
Jan 02 2010
using scroogle
For completeness, my post below should have pointed to the scroogle search engine which purportedly allows you to search google without google being able to profile you. Neat idea if you must use google (why?) but it still fails the Hal Roberts test of what to do if the intermediate search engine is prepared to …
Permanent link to this article: https://baldric.net/2010/01/02/using-scroogle/
Oct 15 2009
where has my money gone
Like most ‘net users I know these days, I conduct most of my financial transactions on-line. But on-line banking is a high risk activity, particularly if you use the “default” OS and browser combination to be found on most PCs. I don’t, but that doesn’t make me invulnerable, just a slightly harder target. So attempts …
Permanent link to this article: https://baldric.net/2009/10/15/on-line-banking-security/
Sep 20 2009
wordpress security
At about the time I decided to move trivia to my own VPS, there was a lot of fuss about a new worm which was reportedly exploiting a vulnerability in all versions <= 2.8.3. Even the Grauniad carried some (rather inaccurate) breathless reporting about how the wordpress world was about to end and maybe we …
Permanent link to this article: https://baldric.net/2009/09/20/wordpress-security/
Sep 12 2009
wordpress on lighttpd
I have commented in the past how I prefer lighttpd to apache, particularly on low powered machines such as the slug. I used to be a big apache fan, in fact I think I first used it at version 1.3.0 or maybe 1.3.1, having migrated from NCSA 1.5.1 (and before that Cern 3.0) back in …
Permanent link to this article: https://baldric.net/2009/09/12/wordpress-on-lighttpd/
Aug 26 2009
wordpress woes
As is common with many blogs, my public ramblings on this site are made possible through the ease of use and flexibility of the mysql/php based software known as wordpress.. And again, as is common to much php/mysql based software, that package has vulnerabilities – sometimes serious, remotely exploitable vulnerabilities. When vulnerabilities are made public, …
Permanent link to this article: https://baldric.net/2009/08/26/wordpress-woes/
Aug 02 2009
zf05
I really missed the old phrack magazine. Some of the “loopback” entries in particular are superb examples of technical nous, complete irreverance and deadpan humour. One of my favourites (from phrack 55) appears in my blogroll under “network (in)security”. I am particularly fond of the observation that details of how to exploit old vulnerabilities are …
Permanent link to this article: https://baldric.net/2009/08/02/zf05/
Jul 05 2009
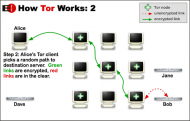
tor on a vps
I value my privacy – and I dislike the increasing tendency of every commercial website under the sun to attempt to track and/or profile me. Yes, I know all the arguments in favour of advertising, and well targeted advertising at that, but I get tired of the Amazon style approach which assumes that just because …
Permanent link to this article: https://baldric.net/2009/07/05/tor-on-a-vps/
Mar 29 2009
bad science and worse
I’m a big fan of Ben Goldacre’s “bad science” column in the Guardian. He is particularly scathing about quackery and spurious medical science. His views of “Dr” Gillian McKeith in particular are well worth reading. Whilst I was reading one of his columns recently, I was reminded of another “Dr” who seems to get away …
Permanent link to this article: https://baldric.net/2009/03/29/bad-science-and-worse/
Dec 24 2008
and yet more DNS lunacy
A company called Unified Root is offering to register new top level domains in advance of the proposed ICANN changes. The company describes itself in the following terms: “UnifiedRoot (Unified Root) is an independent, privately owned company, based in Amsterdam, which makes corporate and public top-level domains (TLDs) available worldwide. Through our own efforts and …
Permanent link to this article: https://baldric.net/2008/12/24/and-yet-more-dns-lunacy/
Dec 24 2008
more DNS silliness
I came across an interesting post on Avert labs site recently. That post pointed to an earlier SANS posting, which in turn, referenced a Symantec discussion of a new Trojan called Trojan.Flush.M. This trojan is an interesting variant of a class of trojans which hijack local DNS settings to force the compromised machine to use …
Permanent link to this article: https://baldric.net/2008/12/24/more-dns-silliness/
Sep 25 2008
gun, foot, shoot
As a chartered member of the British Computer Society (BCS) I recently received through the post my voting forms for the 2008 AGM. The process gives me the option of voting electronically using a website run by Electoral Reform Services. My security codes (two separate numeric IDs, one of six characters, the other of four) …
Permanent link to this article: https://baldric.net/2008/09/25/gun-foot-shoot/
Sep 12 2008
webanalytics – just say no
I have just built myself a new intel core 2 duo based machine to replace one of my older machines which was beginning to struggle under the load of video transcoding I was placing upon it. The new machine is based on an E8400 and is nice and shiny and fast. Because it is a …
Permanent link to this article: https://baldric.net/2008/09/12/webanalytics-just-say-no/