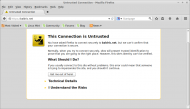
Back in June 2015 I decided to force all connections to trivia over TLS rather than allow plain unencrypted connections. I decided to do this for the obvious reason that it was (and still is) a “good thing” (TM). In my view, all transactions over the ‘net should be encrypted, preferably using strong cyphers offering …
Category: network (in)security
Permanent link to this article: https://baldric.net/2018/07/07/re-encrypting-trivia/
May 12 2017
using a VPN to take back your privacy
With the passage into law of the iniquitous Investigatory Powers (IP) Bill in the UK at the end of November last year, it is way past time for all those who care about civil liberties in this country to exercise their right to privacy. The new IP Act permits HMG and its various agencies to …
Permanent link to this article: https://baldric.net/2017/05/12/using-a-vpn-to-take-back-your-privacy/
Jan 24 2016
guest network
Last month Troy Hunt posted an interesting comment on his blog about the problems around the etiquette of allowing guests onto your home wifi network. In his post, Hunt notes that guests can be deeply offended at being refused access. This is understandable. If they are guests in your home then they are probably close …
Permanent link to this article: https://baldric.net/2016/01/24/guest-network/
Oct 29 2015
lancashire police fail
This is simply depressing. Today I received a classic phishing attack email – the sort I normally bin without thought. According to virustotal, the attachment, which purported to be an MS Word document called “Invoice 7500005791.doc”, was a copy of W97M/Downloader, a word macro trojan which Symantec says is a downloader for additional malware. So …
Permanent link to this article: https://baldric.net/2015/10/29/lancashire-police-fail/
Aug 20 2015
update to domain privacy
At the end of last month I noted that I had been receiving multiple emails to each of the proxy addresses listed for my newly registered “private” domains. Intriguingly, whilst I was receiving at least three or four such emails a week before I wrote about it, I have had precisely zero since. Probably coincidence, …
Permanent link to this article: https://baldric.net/2015/08/20/update-to-domain-privacy/
Jul 30 2015
get your porn here
Dear Dave is at it again. Sometimes I worry about our PM’s priorities. Not content with his earlier insistence that UK ISPs must introduce “family friendly (read “porn”) filters”, our man in No 10 now wants to “see age restrictions put into place or these (i.e. “porn”) websites will face being shut down”. El Reg …
Permanent link to this article: https://baldric.net/2015/07/30/get-your-porn-here/
Jul 28 2015
domain privacy?
Over the past few months or so I have bought myself a bunch of new domain names (I collect ’em….). On some of those names I have chosen the option of “domain privacy” so that the whois record for the domain in question will show limited information to the world at large. I don’t often …
Permanent link to this article: https://baldric.net/2015/07/28/domain-privacy/
Jun 02 2015
de-encrypting trivia
Well, that didn’t last long. When I decided to force SSL as the default connection to trivia I had forgotten that it is syndicated via RSS on sites like planet alug. And of course as Brett Parker helpfully pointed out to me, self-signed certificates don’t always go down too well with RSS readers. He also …
Permanent link to this article: https://baldric.net/2015/06/02/de-encrypting-trivia/
Jun 01 2015
encrypting trivia
In my post of 8 May I said it was now time to encrypt much, much more of my everyday activity. One big, and obvious, hole in this policy decision was the fact that the public face of this blog itself has remained unencrypted since I first created it way back in 2006. Back in …
Permanent link to this article: https://baldric.net/2015/06/01/encrypting-trivia/
Nov 27 2014
independent hit
On trying to reach the website of the Independent newspaper today (the Grauniad is trying my patience of late), I received the following response: Closing the popup takes you to this page: I haven’t checked whether this is simply a DNS redirect or an actual compromise of the Indy site, but however the graffiti was …
Permanent link to this article: https://baldric.net/2014/11/27/independent-hit/
Apr 16 2014
nsa operation orchestra
In February of this year, Poul-Henning Kamp (a.k.a “PHK”) gave what now looks to be a peculiarly prescient presentation as the closing keynote to 2014’s FOSDEM. In the presentation (PDF), PHK posits an NSA operation called ORCHESTRA which is designed to undermine internet security through a series of “disinformation” or “misinformation”, or “misdirection” sub operations. …
Permanent link to this article: https://baldric.net/2014/04/16/nsa-operation-orchestra/
Apr 16 2014
more heartbleed
For any readers uncertain of exactly how the heartbleed vulberability in openssl might be exploitable, Sean Cassidy over at existential type has a good explanation. And if you find that difficult to follow, Randall Munroe over at xkcd covers it quite nicely. My thanks, and appreciation as always, to a great artist. Of course, Randall …
Permanent link to this article: https://baldric.net/2014/04/16/more-heartbleed/
Apr 08 2014
heartbleed
This is nasty. There is a remotely exploitable bug in openssl which leads to the leak of memory contents from the server to the client and from the client to the server. In practice this means that an attacker can read 64K chunks of memory on a vulnerable service, thus potentially exposing security critical information. …
Permanent link to this article: https://baldric.net/2014/04/08/heartbleed/
Feb 12 2014
checking client-side ssl/tls
At the tail end of last year I mentioned a couple of tools I had used in my testing of SSL/TLS certificates used for trivia itself and my mail server. However, that post concentrated on the server side certificates and ignored the security, or otherwise, offered by the browser’s configuration. It is important to know …
Permanent link to this article: https://baldric.net/2014/02/12/checking-client-side-ssltls/
Jan 20 2014
thrust update
I have just run a search for further evidence of the possible compromise at thrustvps and found threads on webhostingtalk, vpsboard, freevps.us and habboxforum amongst others. All of those comments are from people (many, like me, ex-customers) who have received emails like the one I referred to below. So, I guess thrust /do/ have a …
Permanent link to this article: https://baldric.net/2014/01/20/thrust-update/
Jan 18 2014
thrustvps compromised?
I have not used thrust since my last contract expired. I left them because of their appalling actions at around this time last year. However, today I received the following email from them: From: Admin To: xxx@yyy Subject: Damn::VPS aka Thrust::VPS Date: Sat, 18 Jan 2014 03:28:06 +0000 This is a notification to let you …
Permanent link to this article: https://baldric.net/2014/01/18/thrustvps-compromised/
Dec 10 2013
ssl cipher check
My recent explorations of how to strengthen the ssl/tls certificates I use on both trivia and my mail service have given me cause to look for tools to help me test my configuration. The Calomel firefox plugin and sslabs site are very useful for checking HTTPS configurations, but they are fairly specifically aimed at that …
Permanent link to this article: https://baldric.net/2013/12/10/ssl-cipher-check/
Sep 20 2013
that’s another password I have to change
Michael Horowitz has posted an interesting article over at Computer world. In it he points out that, by default, most android devices (tablets and ‘phones) routinely ‘phone home to Google to back up Wi-Fi passwords along with other assorted settings. Google sells this option as a convenience to help you regain settings after you upgrade …
Permanent link to this article: https://baldric.net/2013/09/20/thats-another-password-i-have-to-change/
Sep 10 2013
tor node upgrade
I have switched my tor node to the experimental branch and it is now running version 0.2.4.17-rc. The huge load on the network seen since the botnet starting using it on about 19 August last has forced the tor project team to recommend that all relay operators move to the 0.2.4 branch (and this release …
Permanent link to this article: https://baldric.net/2013/09/10/tor-node-upgrade/
Aug 23 2013
thank you citizen
Imagine Dave’s censorship (^W) surveillance program outsourced to G4S.
Permanent link to this article: https://baldric.net/2013/08/23/thank-you-citizen/
Aug 10 2013
tor users under attack
The Tor network does not just provide anonymous internet access, it also provides for so-called hidden services. These services are not visible outside the Tor network and are only reachable over Tor. The servers are given Tor specific addresses of the form “xyz123.onion” (actually, the addresses are a little more complicated than that because the …
Permanent link to this article: https://baldric.net/2013/08/10/tor-users-under-attack/
Aug 03 2013
security failure at digital ocean
This morning I received an email from Digital Ocean titled “Avoid Duplicate SSH Host Keys”. The email said: “If you have created an Ubuntu Droplet or snapshot prior to July 2nd, DigitalOcean recommends regenerating the SSH host keys. Droplets based on standard images now create unique SSH host keys.” (This, of course, implies that they …
Permanent link to this article: https://baldric.net/2013/08/03/security-failure-at-digital-ocean/
Jul 26 2013
soldier available cross magnet
I am in the process of changing passwords on a bunch of different systems/applications and have been pondering my algorithms, so to speak. Like my friend David, I have an internal model of varying password schemes which I can use in different places. This means that I can happily pick a password for a low …
Permanent link to this article: https://baldric.net/2013/07/26/soldier-available-cross-magnet/
Jul 26 2013
how not to hide
I have written several times in the past about the tedious crud which hits my blog spam filters. Of late I have seen an increase in spam which looks, at first sight, plausible comment, but on closer inspection turns out to have the usual links to sites flogging cheap copies of western luxury goods. A …
Permanent link to this article: https://baldric.net/2013/07/26/how-not-to-hide/