It would seem that Microsoft has been taking a look at the world of linux and decided that the best way to take on the emerging desktop threat is to emulate the competition. Unfortunately for them, they seem to have decided to emulate the stupidest of decisions recently taken by Canonical and have completely redesigned the windows desktop interface in windows 8 to make it look like a mobile phone. [Note, that link goes to techradar. I would link to the official windows 8 pages, but they insist on using silverlight….].
When I first saw the early reviews of the new metro interface I couldn’t quite believe that Microsoft (who are not usually suicidal) could have made a mistake which so completely dwarfs the vista experience. So I downloaded a copy of the release preview and fired it up in a virtualbox VM. I chose the iso installation option because MS do not have the equivalent of a linux live distro and, since I do not run Microsoft software, the option of a live install is, fortunately, impossible for me. I say fortunately, because I cannot believe that anyone who selected that option and overwrote a working version of windows 7 will be at all happy.
Not that the iso install option was straightforward either. Microsoft, being Microsoft, cannot allow you to simply try out a pre-release version of their software, Instead, they make you jump through all sorts of unnecessary hoops to register and set up an account which will give you access to their on-line software repository. Why, is completely beyond me. I had to give MS a name, postcode, date of birth, gender, the name of my first pet and two, yes two, separate email accounts before they would let me in. Even then, I couldn’t successfully complete registration (OK, I may not have been entirely truthful in my registration details, but two separate trashmail accounts should have been enough). The last hurdle I faced was the “click this link to confirm your account” sent to the first of the two email addresses I gave. Clicking on that link took me to a windows live sign in page – and there, of course, I got stuck. MS wouldn’t let me sign in using FF on linux, saying, unhelpfully:
“The Windows Live Network is unavailable from this site for one of the following reasons:
- This site may be experiencing a problem
- The site may not be a member of the Windows Live Network.
You can:
You can sign in or sign up at other sites on the Windows Live Network, or try again later at this site.”
Now if the windows 8 installation in my VM had allowed cut and paste from my desktop (as is possible with a linux VM) I could have just pasted the login URL into IE and continued from there. But no, not possible, and I really could not be bothered to transcribe a 177 character long random URL by hand. I wasn’t that interested in continuing.
Here’s why:
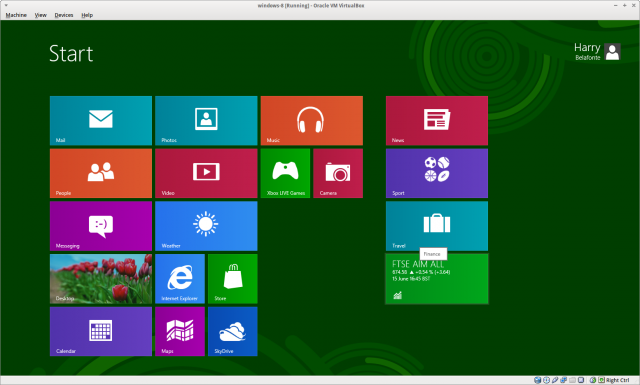
And this is what you see if you click on the “desktop” icon:
What happened to the task bar and the infamous “Start button”?
That interface is not going to go down at all well even with domestic users, let alone businesses which may have invested significant time, effort and money in previous versions of windows.
Ironically, one of the arguments used against moving from windows to a linux desktop in the enterprise is the “cost of change” notably in the cost of staff training. It looks to me as if Microsoft may just have handed the open source community its best ever opportunity to move into space previously sewn up by Redmond.
(Oh, and BTW, windows 8 is painfully slow in a VM).