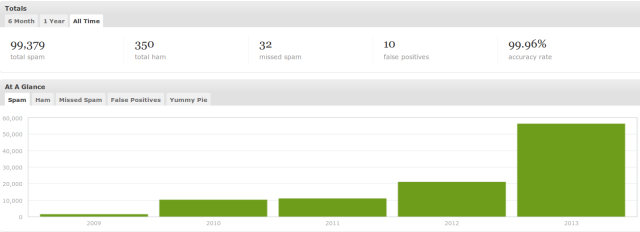
The past couple of days have seen a flurry of news stories about Tor. Some of the news has hit the mainstream media, some of it hasn’t. Yet.
A couple of day ago, a rather plaintive post to the tor-talk mailing list read:
“looking for a way to contact silk road.Site shut down.money at stake.”
(Note to readers – the “silk road” was a somewhat notorious website acting as a broker, or intermediary, between persons wishing to purchase materials of questionable legality, such as high grade drugs or weapons and vendors of said materials. Transactions on the site were conducted using bitcoin. The site operator made his money by taking a transaction fee from the bitcoin traffic. The “silk road” was run as a hidden service on the Tor network.)
In response to this query, another poster pointed to an article in ehackingnews which explained that the site had been taken down by the FBI following a fairly lengthy, (and by all accounts fairly thorough) investigation. One Ross Ulbricht, the alleged operator of the silk road site has been arrested by the FBI. The full account of the FBI investigation, and its case against Ulbricht can be seen (warning, PDF) here.
After this post, there then follows a long series of posts in the thread titled “Silk Road taken down by FBI”. This thread bears reading. Aside from some of the usual rabid Aluminium Foil Deflector Beanie nonsense, or expected anti-establishment ranting, there is some thoughtful and useful commentary. Two things struck me when reading this series of posts. First, the FBI takedown and arrest seems to have resulted from some good, old fashioned, thorough police work (helped, of course, by the admitted stupidity and poor operational security demonstrated by Ulbricht). As one poster said:
In many ways this is (or should be) a PR win for Tor.
1) No technical vulnerabilities were used (AFAWK) – this should be welcome news to Tor users
2) Traditional police work still works – this should be good news to the law and order folks that traditional methods still work and no extensive digital survailance (sic) state is needed.
Secondly, this incident, coupled with what is now known to be the FBI takedown in August of this year of the Freedom Hosting Service (also a Tor hidden service) site allegedly hosting child pornography, means that two fairly high profile, (probably) illegal sites are now off the Tor network.
I say “probably” for two reasons, one, I am not a lawyer, and two, I am relying on third party reporting of the activity on those sites. I have no personal knowledge of either of them. Here, though, I must confess to some mixed feelings in my reaction. On the one hand I must applaud the removal of sites which have given rise to the sort of reporting which has increasingly lead to Tor becoming known as the “dark web”, a home for criminal activity and only criminal activity. This sort of reporting fosters an atmosphere which is antithetical to support for Tor. That cannot be a good thing, particularly at a time when personal privacy and anonymity are under increasing threat. On the other hand, I believe, and have argued elsewhere that Tor is and should be completely neutral with respect to the services it hosts or provides access to. It is for wider society to take a judgement on which of those services are tolerable. Tor operators must remain neutral or we fall into the same trap of censorship which we profess to deplore elsewhere.
Then, just as the feverish temperature on the tor-talk list was about to cool slightly, Roger Dingledine lobbed in a new post yesterday pointing to the latest in the series of Guardian articles on the Snowden revelations. Those articles, which are listed in summary here detail how the NSA and GCHQ have been attacking Tor in attempts to de-anonymise its users. Dingledine has since posted a blog article on the torproject website explaining that, yes, they do know about the Guardian reporting, in fact they contributed to that reporting. Dingledine promises a full analysis later, but meanwhile he points to his commentary in the Guardian article, where he says (of the NSA):
“The good news is that they went for a browser exploit, meaning there’s no indication they can break the Tor protocol or do traffic analysis on the Tor network. Infecting the laptop, phone, or desktop is still the easiest way to learn about the human behind the keyboard.
Tor still helps here: you can target individuals with browser exploits, but if you attack too many users, somebody’s going to notice. So even if the NSA aims to surveil everyone, everywhere, they have to be a lot more selective about which Tor users they spy on.
Just using Tor isn’t enough to keep you safe in all cases. Browser exploits, large-scale surveillance, and general user security are all challenging topics for the average internet user. These attacks make it clear that we, the broader internet community, need to keep working on better security for browsers and other internet-facing applications.”
As Dingledine says, the good news from Tor’s perspective is that even an adversary as large, powerful and well funded as the NSA is apparently unable to break the network itself. This means that Tor remains safe to use by that majority of people whose only concern is a much lesser adversary. It is also worth noting that there is no contradiction between NSA’s apparent failure in direct attacks against the Tor network and the FBI’s successes against criminal activity facilitated by Tor (even if, as some suspect, the FBI had NSA assistance – see the “parallel construction” arguments). The FBI success proves that police investigative activity works. If you are a dumb criminal, then no technology is going to help you.