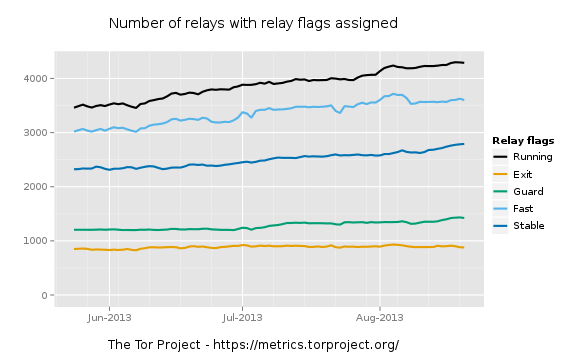
The Tor network does not just provide anonymous internet access, it also provides for so-called hidden services. These services are not visible outside the Tor network and are only reachable over Tor. The servers are given Tor specific addresses of the form “xyz123.onion” (actually, the addresses are a little more complicated than that because the identifier portion of the address is the first 10 bytes of the SHA-1 digest of an ASN.1 encoded version of the RSA public key for the service – but you get the picture I’m sure.) This naming convention has led to the servers being known as “onions”
On the 4th of August a correspondent on the tor-talk email list posted a message saying:
Noting what is apparently a very large drop in the number of onions online. Still checking…
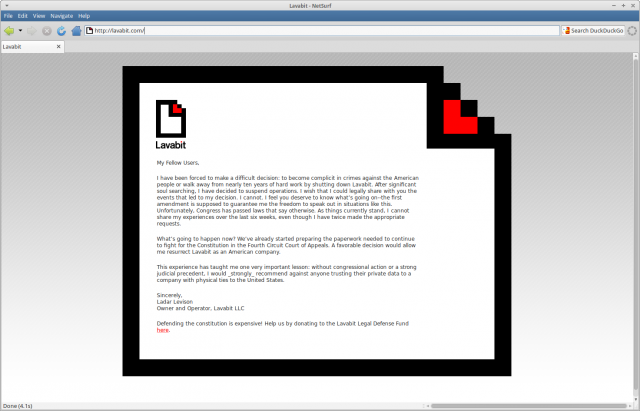
In response another correspondent posted a reference to the reddit site discussing the recent arrest of the founder of the “Freedom Hosting” sites. Freedom Hosting was apparently widely used for hosting .onions, and allegedly, some of those sites were used to host child pornography. Another correspondent sent a reference to the openwatch post of 4 August which reported that the owner of Freedom Hosting had been arrested in Ireland and was being held pending an FBI extradition request to the USA. It also reported that malicious JavaScript had been discovered on a number of hidden (onion) services.
An early official posting about the incident from the torproject came late on the 4th and was posted to tor-talk on the 5th of August. In that post, phobos said:
The person, or persons, who run Freedom Hosting are in no way affiliated or connected to The Tor Project, Inc., the organization coordinating the development of the Tor software and research.
That was important, and needed to be said because there was already evidence of some confusion about the status of Freedom Hosting and indeed of hidden services in general. The fact is that the Tor network is simply an enabling mechanism for such services and the project itself has no control over who hosts services, where or why they host them or who uses them. That is the whole point of an anonymous network. It is anonymous.
Phobos went on:
In the past, adversarial organizations have skipped trying to break Tor hidden services and instead attacked the software running at the server behind the dot onion address. Exploits for PHP, Apache, MySQL, and other software are far more common than exploits for Tor. The current news indicates that someone has exploited the software behind Freedom Hosting. From what is known so far, the breach was used to configure the server in a way that it injects some sort of javascript exploit in the web pages delivered to users. This exploit is used to load a malware payload to infect user’s computers. The malware payload could be trying to exploit potential bugs in Firefox 17 ESR, on which our Tor Browser is based. We’re investigating these bugs and will fix them if we can.
As for now, one of multiple hidden service hosting companies appears to be down. There are lots of rumors and speculation as to what’s happened. We’re reading the same news and threads you are and don’t have any insider information. We’ll keep you updated as details become available.
A later posting, on 5 August, expanded on the first post, saying that:
An attack that exploits a Firefox vulnerability in JavaScript has been observed in the wild. Specifically, Windows users using the Tor Browser Bundle (which includes Firefox plus privacy patches) appear to have been targeted.
That post also pointed to a full advisory from Roger Dingledine at torproject. In that advisory. Dingledine notes:
In principle, all users of all Tor Browser Bundles earlier than the above versions are vulnerable. But in practice, it appears that only Windows users with vulnerable Firefox versions were actually exploitable by this attack.
To be clear, while the Firefox vulnerability is cross-platform, the attack code is Windows-specific. It appears that TBB users on Linux and OS X, as well as users of LiveCD systems like Tails, were not exploited by this attack.
He describes the impact of the attack thus:
The vulnerability allows arbitrary code execution, so an attacker could in principle take over the victim’s computer. However, the observed version of the attack appears to collect the hostname and MAC address of the victim computer, send that to a remote webserver over a non-Tor connection, and then crash or exit. The attack appears to have been injected into (or by) various Tor hidden services, and it’s reasonable to conclude that the attacker now has a list of vulnerable Tor users who visited those hidden services.
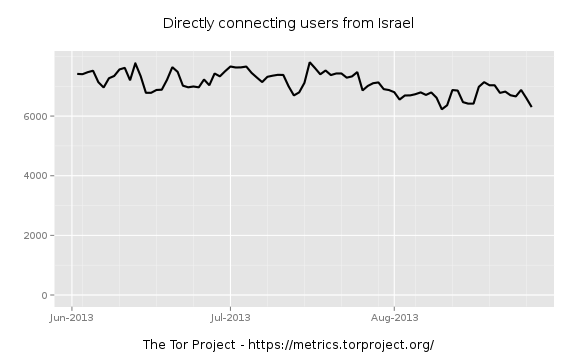
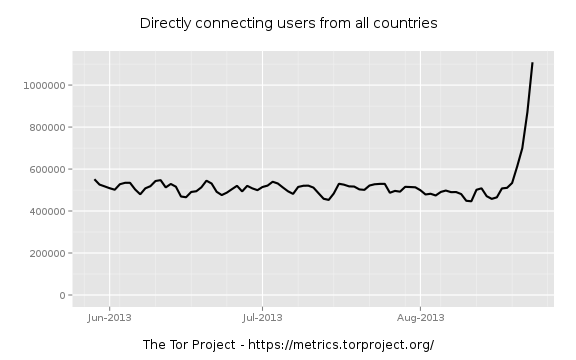
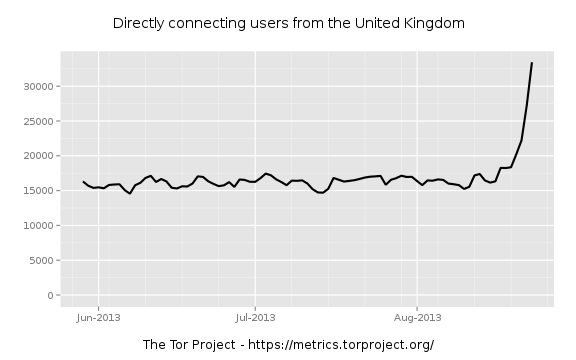
In the ensuing, rather confused, round of post and counter post a couple of things became clear. Firstly, the tinfoil beanie hat brigade (TFBHB) were out in force. Speculation as to the source [*] of what was later to become termed “torspolit” was rife, ranging from the NSA or FBI to the Hacker group Anonymous (who it must be said had form with Freedom Hosting having attacked it in the past because of its alleged hosting of child pornography) or even to the owner of Freedom Hosting himself. Secondly, there was increasing concern about the continued validity and utility of Tor as a trustworthy anonymising tool (“is Tor still valid?”).
Many commentators (e.g. Chakravarty, Stavrou and Keromytis or Salo) in the past have noted that Tor is vulnerable to a “Global Passive Adversary” (or GPA – someone who can observe all internet traffic). If the existence of a GPA is accepted then it could reasonably be postulated that such an adversary would be capable of de-anonymising Tor users – largely through traffic analysis alone. However, until recently, the actual existence of such a capable adversary was in some doubt, though there was no doubt that some countries were in a position of de-facto GPA in their local domain (e.g. China with respect to its population).
What seemed to have been less expected was that an adversary would launch an active attack such as “torsploit” with the aim of de-anonymising Tor users. It is this latest attack which seems to have brought the TFBHB out in such force. In the rather febrile atmosphere post Snowden, any such visible attack on Tor users begins to look highly suspicious, particularly if that attack is aimed simply at identifying end users of Tor hidden services. When early analysis of “torsploit” identified the hard coded IP address in the exploit as belonging to US defense contractor SAIC and geolocation of the IP address allegedly corresponded to an SAIC facility in Arlington, Virginia, every TFBHB member on the ‘net screamed “NSA”. Over at El Reg, the conspiracy theorists had a field day (I particularly liked one comment which asked “how long until it turns out that Snowden allegedly owns those IP addresses”).
Since that early analysis by Baneki Privacy Labs and VPN provider Cryptocloud, the researchers have backed off a little from their claims that there is a heavily smoking gun. A post by Cryptocloud dated 7 August says that they no longer believe that they can conclusively state that the IP address in question was allocated by SAIC to the NSA.
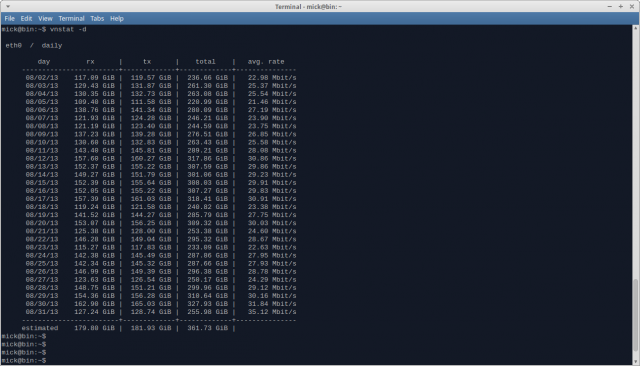
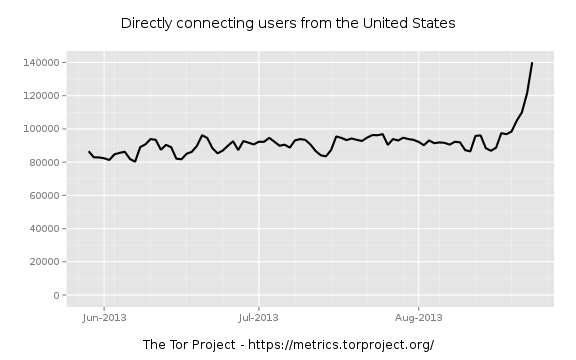
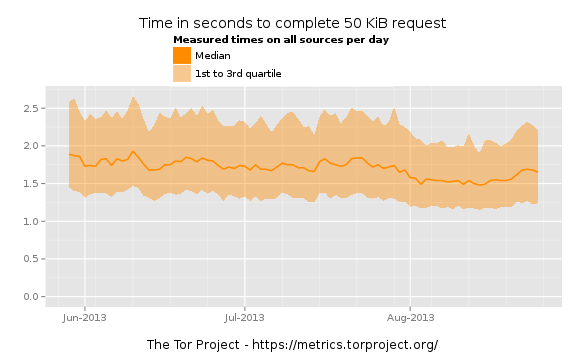
Whilst the jury may yet be out on the identity of the actual “torsploit” actors, the impact they have had on actual Tor usage seems likely to be minimal. Yesterday, 9 August, tails 0.20 was released. Whilst tails users themselves would not have been vulnerable to the attack, tails 0.20 fixed several security issues which had been identified in tails 0.19. On checking my own tails mirrors last night I noticed that one was transmitting at a mean rate over 90 Mbit/s (normal mean around 10-12 Mbit/s) the other was running at around 65 Mbit/s (normal mean 7-9 Mbit/s). If my experience is typical of the other mirrors, then tails usage looks to be fairly healthy in future.
I think Tor is here to stay.
[*] Update added 14 September 2013.
According to this report in wired.com, pointing to a report in the Irish Independent of 12 September, the FBI admitted in Court in Ireland that it was behind the seizure of the Freedom Hosting servers. The wired article also implies that the FBI were responsible for the “torsploit” malware attack. However, this claim is not supported by any reporting in the original Irish Independent article.